What is OT and why is it important?
Operational technology (OT) refers to the hardware and software systems used to monitor, control, and automate industrial processes in sectors like energy, water supply, and transportation. Unlike traditional IT systems, which manage data and business applications, OT interacts directly with physical equipment such as power grids, water treatment plants, and industrial control systems.
In critical infrastructure, OT ensures that essential services remain operational. Systems like SCADA (supervisory sontrol and data acquisition), PLC (programmable logic controllers), and RTU (remote terminal units) are used to regulate energy distribution, monitor gas and water pipelines, and control public transportation networks. These systems must be highly reliable, as disruptions can have far-reaching consequences for public safety and economic stability.
With increasing digitalisation and interconnectivity, OT systems are no longer isolated from external networks. Many now integrate with IT networks for remote monitoring, predictive maintenance, and automation. This convergence improves efficiency but also introduces new security challenges, as OT networks - traditionally designed for reliability over security - are now exposed to cyber threats that can cause physical disruptions.
Common OT communications protocols
In OT, communication protocols are designed to support real-time control, reliability, and efficiency in industrial and critical infrastructure environments. Unlike in IT, where the vast majority of communication occurs over common protocols such as TCP/IP, UDP/IP, OT networks rely on specialised protocols tailored for specific applications. These protocols are often optimised for low-latency control, deterministic behaviour, and legacy hardware compatibility, but many were not designed with security in mind. Below is an overview of four key OT communication protocols widely used in energy infrastructure and industrial automation.
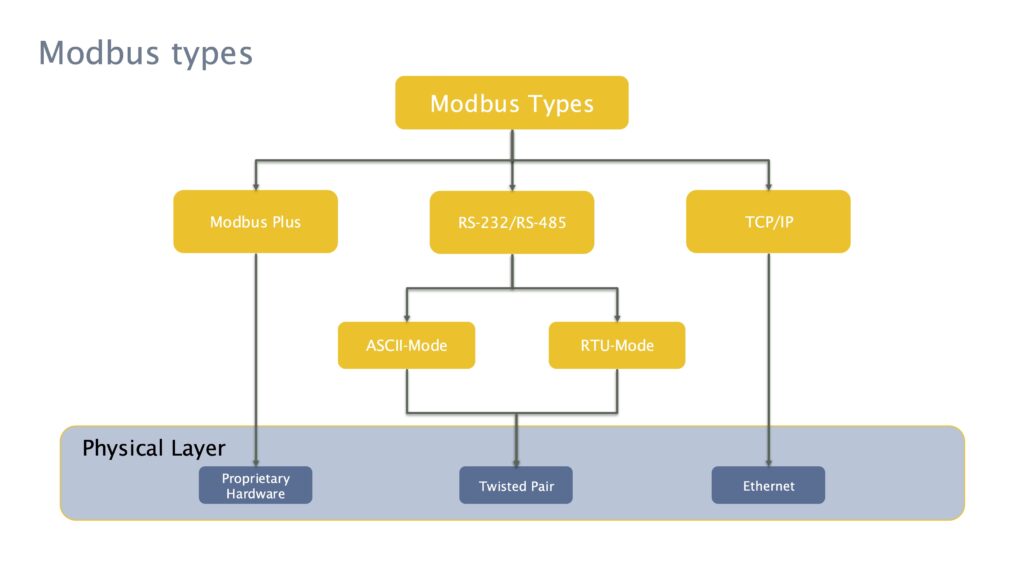
Modbus
Modbus is one of the oldest and most widely used industrial communication protocols. Developed in 1979 by Modicon (now Schneider Electric), it enables communication between programmable logic controllers (PLCs), sensors, and SCADA systems. Modbus exists in two main variants:
- Modbus RTU (uses serial communication)
- Modbus TCP (runs over Ethernet networks)
Application Areas:
- Industrial automation (factories, process control)
- Energy infrastructure (power plants, substations, grid monitoring)
- SCADA systems
M-Bus
M-Bus is a protocol specifically designed for remote reading of utility meters (electricity, water, gas, and heat). It allows utility companies to efficiently collect and manage consumption data from a large number of distributed meters.
Application Areas:
- Smart metering (gas, water, electricity, district heating)
- Utility infrastructure
- Building management systems
IEC 60870-5-104
IEC 60870-5-104 is a standardised SCADA protocol used for power grid control and monitoring, particularly in Europe. It is an IP-based version of IEC 60870-5-101 and allows remote telemetry and control of substations and distribution systems.
Application Areas:
- Power grid SCADA systems
- Transmission and distribution substations
- Energy dispatch centres
IEC 61850
IEC 61850 is a modern protocol for substation automation and smart grids. Unlike traditional protocols that rely on simple data polling, IEC 61850 introduces object-oriented communication and high-speed event-driven messaging (GOOSE and MMS). It is designed to support automation, predictive maintenance, and real-time grid stability.
Application Areas:
- Smart grids and modern substation automation
- High-voltage power transmission and distribution
- Renewable energy integration (solar, wind farms, battery storage systems)
OT security and common threats in OT networks
OT networks are essential for managing industrial processes in energy, utilities, and other critical infrastructure sectors. Unlike IT networks, which are built with security in mind, OT systems have traditionally prioritised reliability and availability over cybersecurity. Many of the protocols and devices in use today were developed decades ago, long before cyber threats became a concern. As a result, these systems often lack fundamental security measures, making them attractive targets for attackers.
One of the most significant vulnerabilities in OT networks is the lack of authentication and encryption. Many widely used industrial communication protocols, such as Modbus, M-Bus, and IEC 60870-5-104, were not designed to verify the identity of devices or users communicating within the network. This means that any system capable of sending properly formatted messages can potentially issue commands to industrial controllers, actuators, or meters. Even more concerning is that these protocols transmit data in plain text, without any encryption, making it easy for attackers to intercept and manipulate communications. For example, in a Man-in-the-Middle (MITM) attack, an attacker could intercept traffic between a control centre and a substation, altering sensor data or injecting false commands. In a replay attack, an attacker could capture and resend a previously valid command, such as a shutdown signal, to disrupt operations. Because these protocols were designed with reliability rather than security in mind, such attacks can go undetected until serious consequences arise.
Beyond communication weaknesses, physical security risks present another major challenge in OT environments. While many assume that industrial control systems are protected by air gaps, meaning they are isolated from external networks, real-world incidents have repeatedly proven otherwise. Physical access points such as USB ports, maintenance laptops, and exposed network interfaces provide direct entry to critical systems. A well-known example is the Stuxnet attack, where malware was introduced into an air-gapped system via infected USB drives, allowing attackers to sabotage industrial centrifuges. Similarly, a malicious insider or an external attacker with brief physical access to a control panel or an industrial Ethernet switch could introduce rogue commands, install malware, or even shut down critical processes.
The combination of unsecured communication protocols and weak physical security controls makes OT networks highly susceptible to cyberattacks. Unlike IT breaches, where the primary concern is data theft, attacks on OT systems can lead to power outages, water supply disruptions, or even physical damage to industrial machinery. As the integration between OT and IT systems continues to grow, securing these environments becomes an urgent priority.
Monitoring Modbus: Detecting and mitigating rogue devices in power infrastructure
Let's assume a local energy provider operates a power distribution network managed by a SCADA system that communicates with remote substations, circuit breakers, and monitoring devices over a Modbus TCP/IP network. What are the potential security risks and consequences if an attacker gains unauthorised access to the network and how could a SIEM system help detect and mitigate the threat?
Modbus: How it works, network topology, and security risks

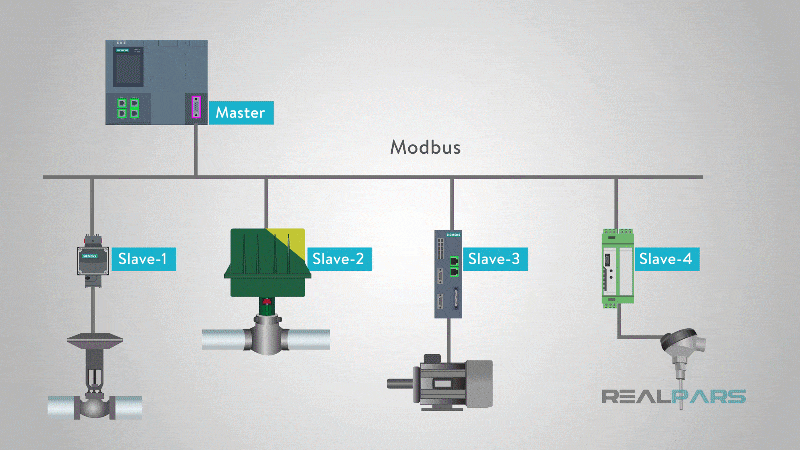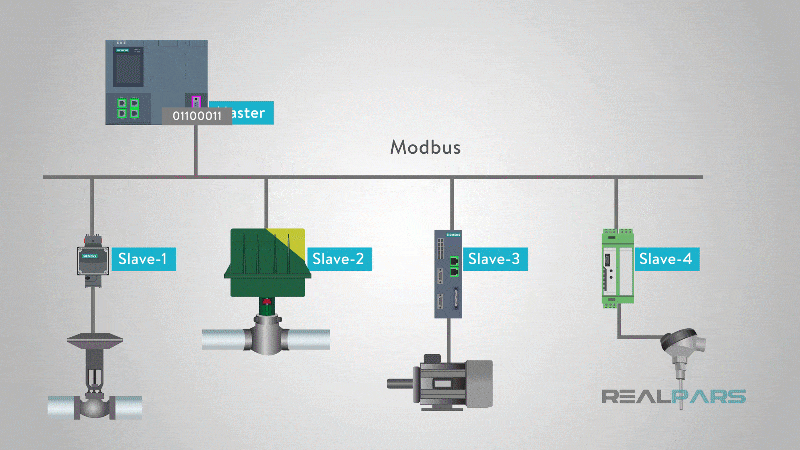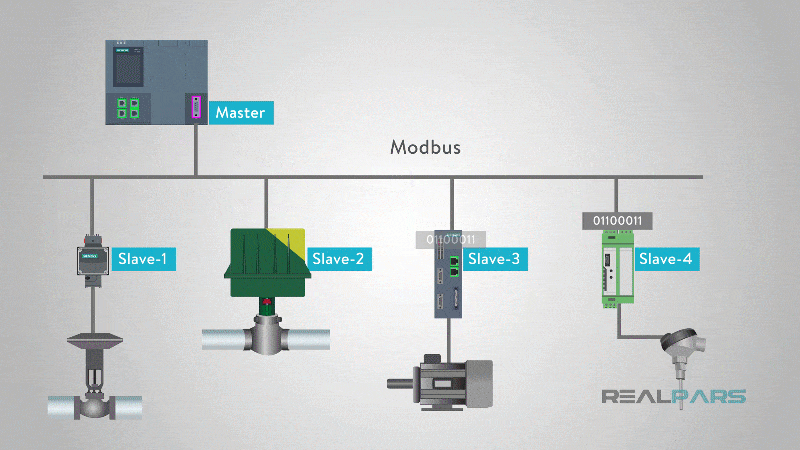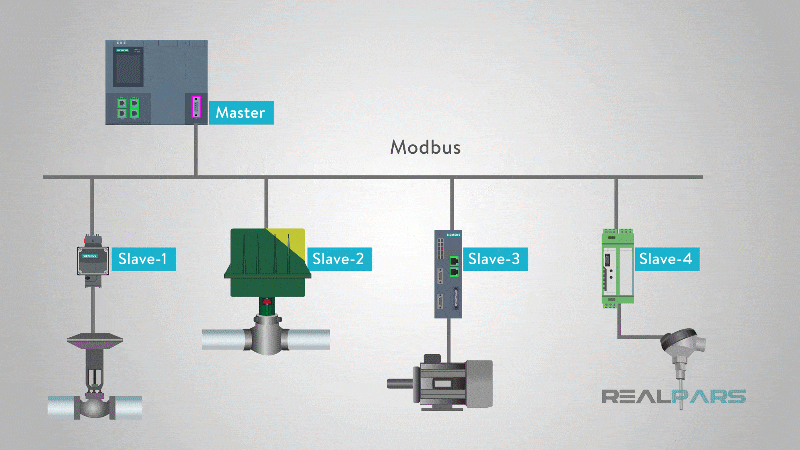
Modbus has a master-slave architecture, where a central device (master) sends requests to one or more subordinate devices (slaves) and awaits responses. These requests can include reading sensor data, modifying device settings, or controlling actuators. The blog post on Realpars.com provides a comprehensive explanation of how Modbus works.
The protocol operates in two main variants:
- Modbus RTU (remote terminal unit): Uses serial communication (RS-232 or RS-485), often seen in legacy systems.
- Modbus TCP: Uses Ethernet networks, allowing for easier integration with modern OT and IT systems.
In a typical Modbus network topology, a SCADA system or control server acts as the master, while multiple field devices-such as PLCs, sensors, meters, and RTUs-function as slaves. Communication is direct and unencrypted, meaning that any device on the network can send or modify data if it has access.
The threat: A malicious or infected Modbus device in the network
Let's consider a scenario where an attacker introduces a rogue Modbus slave device into the network of our ficticious energy provider. This rogue device could be a compromised sensor, meter, or a PLC acting as a slave. Since Modbus does not include authentication or device verification, any device connected to the network can respond to Modbus requests if it knows the expected format.
How a Rogue Modbus Slave Can Exploit the Network
- Spoofing legitimate devices: The rogue slave could impersonate an existing, trusted device by using its address and responding to requests with falsified data. If the real device is still online, the attacker could race to respond first, feeding operators incorrect readings. Example: A rogue temperature sensor reports normal values, masking an actual overheating issue in a substation.
- Flooding the network with fake responses: A rogue slave could continuously respond to Modbus queries, overwhelming the master and making it difficult for legitimate devices to communicate. Example: A malicious device sends thousands of responses per second, causing latency and operational delays.
- Passive Data Exfiltration (eavesdropping on queries): Even if the rogue device does not actively send malicious responses, it could passively listen to Modbus requests, learning operational details about the grid. Example: The rogue slave logs all SCADA queries, capturing real-time energy distribution data for industrial espionage.
Because Modbus devices inherently trust all network participants, these attacks can go unnoticed unless proper monitoring mechanisms are in place.
How a SIEM can detect and react to a malicious Modbus device
A Security Information and Event Management (SIEM) system plays a crucial role in detecting and responding to threats in an OT network. Since Modbus lacks authentication and encryption, a SIEM can act as a second layer of defence, continuously monitoring network activity, tracking devices, and flagging abnormal behaviour.
Monitoring and inventory of Modbus devices
One of the first security measures a SIEM can provide is building an inventory of legitimate devices in the Modbus network. This can be done in two ways:
- Passive Monitoring: The SIEM listens to normal Modbus traffic, logging which slave devices respond to requests from the master. If a new, unrecognised Modbus slave suddenly appears in the network, the SIEM can raise an alarm, as this could indicate an unauthorised device.
- Active Polling (Inventory Scans): The SIEM can periodically instruct the master to send queries to all possible slave addresses and track their responses. This ensures that only known devices are operating in the network and helps detect unauthorised Modbus slaves in real-time. Additionally, the SIEM can collect device-specific information, such as Modbus function codes supported, register values, and response patterns, helping to identify potential anomalies.
Automated Response & Mitigation
When the SIEM detects a rogue Modbus device, it can trigger various predetermined actions to contain the threat before it escalates:
- Isolation of the Rogue Device: If the SIEM detects a new or suspicious Modbus slave, it can instruct a managed switch to block the device's MAC address or shut down the Ethernet port to prevent further communication.
- Blocking Unauthorized Modbus Commands: The SIEM can integrate with firewalls or intrusion prevention systems (IPS) to block specific Modbus function codes (e.g., unauthorised WRITE commands to critical registers).
- Real-Time Alerts to Security Teams: The SIEM sends high-priority alerts to the Security Operations Centre (SOC), allowing security analysts to manually investigate and confirm the threat.
- Correlation with other security events: If a rogue Modbus device also tries to communicate with an external network, the SIEM can correlate this with firewall logs, identifying potential data exfiltration.
How to retrofit security in a brownfield OT environment
Securing an existing (brownfield) OT environment can be challenging. However, integrating a SIEM system into the OT network can provide real-time visibility, anomaly detection, and automated response without disrupting operations.
Steps to Improve Security in a brownfield OT network
- Deploy a SIEM System
- Ensure the SIEM Access to all OT network segments
- Create a device inventory: Leverage the SIEM to passively map out all existing OT devices and their communication patterns. Identify legacy or undocumented devices that could pose security risks.
- Monitor network traffic continuously: Establish a baseline of normal Modbus/OT traffic to detect deviations and anomalies. Track which devices communicate and how frequently to spot unexpected behaviours.
- Detect and alert on unauthorized devices or behavior: Raise real-time alerts if a new device appears or if an existing device starts acting abnormally. Flag unexpected function codes, unauthorised write attempts, or anomalous response behaviour.
- Automate incident response: Integrate the SIEM with managed switches or firewalls to isolate compromised devices.
By following these steps, brownfield OT networks can achieve a higher level of security without requiring a complete infrastructure overhaul.
Conclusion
Implementing a SIEM system is crucial for securing OT networks in energy infrastructure, especially with the increasing cyber threats targeting Modbus-based systems. A SIEM enables real-time monitoring, anomaly detection, and automated threat response, helping energy providers identify rogue devices, prevent disruptions, and maintain operational integrity.
With extensive expertise in SIEM solutions for energy suppliers, Swissmakers offers tailored security monitoring based on Elasticsearch, providing automated analysis and proactive threat detection. Our SOC-lite service ensures continuous SIEM maintenance, alarm analysis, and incident response, allowing energy providers to focus on their core operations while we safeguard their critical infrastructure.