On 1 July 2024 the amendments to the Electricity Supply Ordinance of 14 March 2008 (StromVV) enter into force. In Article 5a, the ICT minimum standards for practically all Swiss electricity suppliers as binding explains. The short implementation time and lack of resources in the areas of IT personnel, finances and expertise pose a challenge for electricity suppliers. Major challenges.
The following explanations will key points on the new requirements and the ICT minimum standard. It also explains how a SOC and the SIEM system integrated into it can be used in the Support implementation of the measures can.
Changes to the electricity supply laws
In the version of the Federal Electricity Supply Act of 23 March 2007 (Electricity Supply Act, StromVG) valid from 1 July 2024, the Protection against cyber threats by grid operators, generators and storage operators as a new own article into the law:

The Electricity Supply Ordinance of 14 March 2008 (StromVV), the new version of which will also come into force on 1 July 2024, defines the required measures even more precisely:

The Minimum standard to improve the ICT resilience of the Federal Office for National Economic Supply FONES in the version of May 2023 is published as binding declared. It also stipulates that the achievement of the minimum ICT standard in the various Protection levels must be submitted to the Swiss Federal Electricity Commission ElCom upon request.
Protection levels A, B and C
Not sure what level of protection your company needs to fulfil? It's easy to find out:
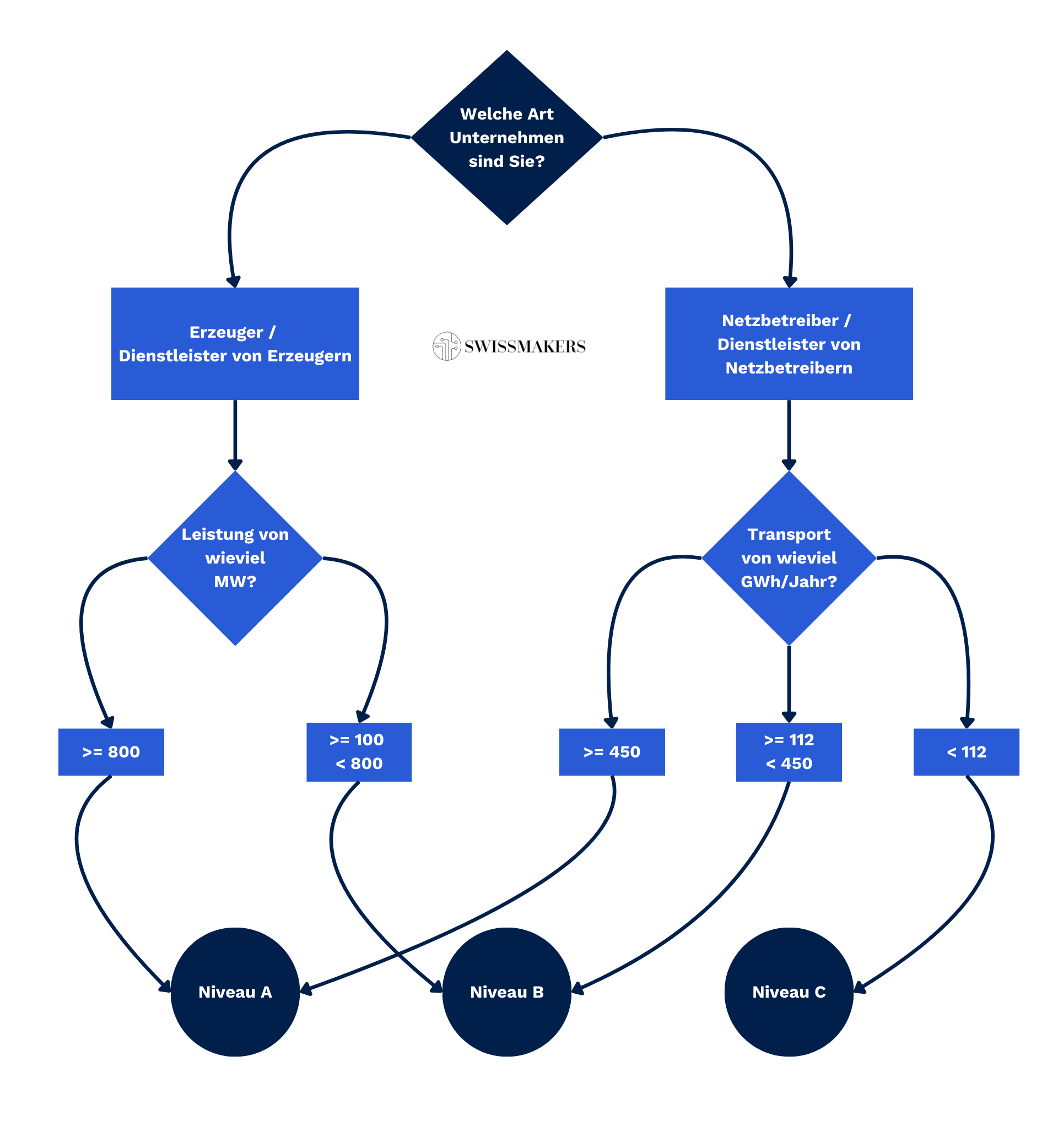
The various levels of protection required to fulfil the ICT minimum standard can be found in Annex 1a of the StromVV. This annex once again describes the categories into which the companies are categorised and provides a list of the minimum values that must be achieved by the various protection levels per measure of the ICT minimum standard.
ICT minimum standard
The minimum standard for improving ICT resilience was developed primarily as support for increasing the Cybersecurity for critical infrastructures Switzerland. However, it can basically serve all companies and organisations as a basis for their IT security. The standard is divided into the following areas:
Introduction Provides explanations and background knowledge.
Realisation 108 specific measures to increase IT security
Examination Procedure for reviewing the measures by the company itself or external parties.
Defence-in-depth strategy
The ICT minimum standard works with the Defence-in-depth strategy. This means that the protection of critical infrastructures multi-layered is built up. The approach pursued is holisticThe aim is to protect all operating resources against any risks with the available resources. Potential future risks should also be considered.
In the critical infrastructures for which the minimum standard was developed, information and communication technology (ICT) is often used in addition to Industrial control systems (ICS) used. The defence-in-depth protection measures also provide security for the ICS. It must be noted that ICT and ICS have different protection requirements, which must be taken into account when implementing the ICT minimum standard (see Table 1 of the standard).
Important Elements of a defence-in-depth strategy are according to Table 2 of the standard:
- Risk Management Programme
- Cybersecurity architecture
- Physical security
- Network architecture
- Network Perimeter Security
- Host Security
- Security monitoring
- Vendor Management
- The human element
Catalogue of measures
The ICT minimum standard is based on the following structure of measures Structure of the NIST Framework. NIST works according to the following scheme:
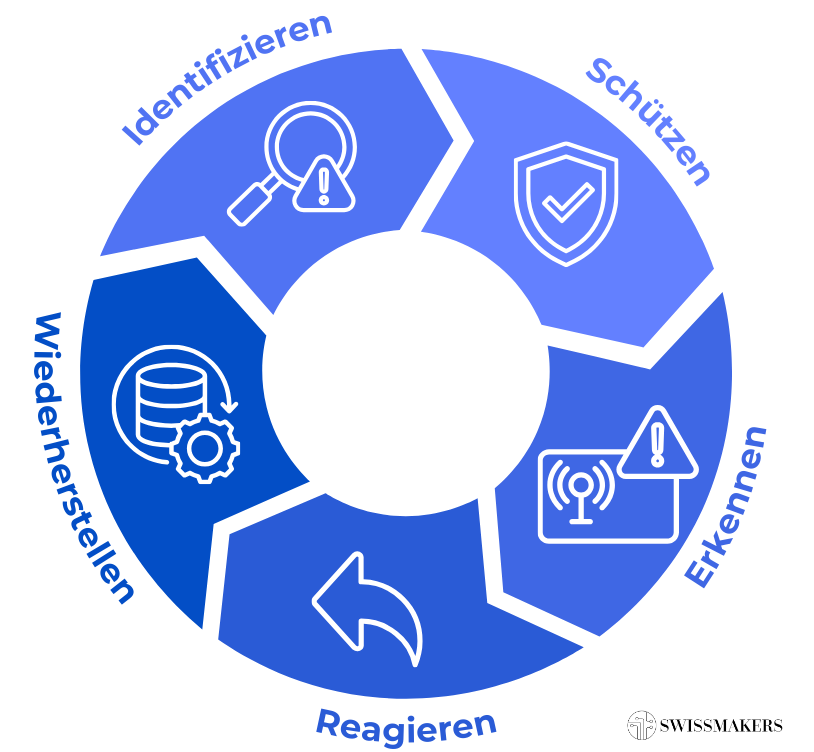
The individual measures in the ICT minimum standard have a clearly identifiable designation and a description of the tasks. In addition, each category contains a table with other information security frameworks and their measures, which can be assigned to the corresponding category of the ICT minimum standard. This allows companies that already have another certification such as ISO 27001 or BSI to clearly recognise which measures they already fulfil and where there may still be room for improvement.
In Annex 1a of the StromVV, each measure Minimum values are listed for each level of protection. These values relate to Part 3 - Testing the ICT minimum standard. The ratings are determined as follows:
0 = not realised
1 = partially implemented, not fully defined and accepted
2 = partially implemented, fully defined and accepted
3 = implemented, fully or largely implemented, static
4 = dynamic, implemented, continuously reviewed, improved
Tier levels 1 to 4 are explained in more detail in chapter 3.2 in the ICT minimum standard.
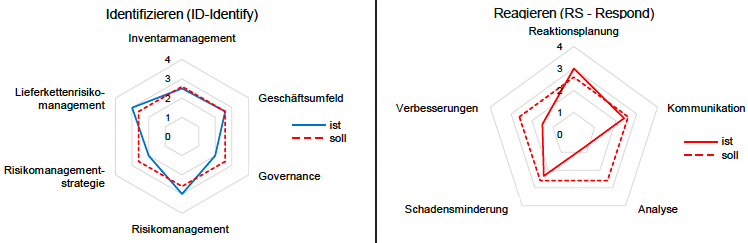
As Assessment tool the Federal Office for National Economic Supply BWL provides an Excel document. The entire tool can be used in English, German, French and Italian. Each measure can be assigned the achieved level 0 to 4 and the assignment to other frameworks is broken down again here for the individual measures. The assessment tool offers Automated (graphical) analyses for overall maturity and maturity per function (see examples below from the ICT minimum standard).
Industry standard electricity
In addition to the minimum standard for improving ICT resilience, which has been developed for all sectors, the Federal Office for National Economic Supply (FONES) also provides standards specifically developed for the various critical infrastructures. For the Current operations consists of the "Basic protection manual for operational technology in the power supply"The manual was prepared by the Association of Swiss Electricity Companies VSE.
The manual for OT in the power supply also follows the defence-in-depth strategy and divides the measures into the five functions of identify, protect, detect, govern and recover. The manual can be used as a Addition to the ICT minimum standard The recommendations are specifically tailored to electricity suppliers. It should be noted that the ICT minimum standard is available in a significantly newer version than the manual.
Role of SIEM and SOC
A Security Operations Centre (SOC) is a central unit within or outside an organisation that focuses on the Continuous monitoring and improvement of the security situation focussed. The SOC team uses tools such as SIEM, XDR and SOAR systems to identify, analyse and process security incidents. There are currently many different views on which services should be provided by a SOC. In this article, we refer to the definition by Mughal (2022), which defines the Core services of a SOC as follows:
- Incident Response (IR)Detect and respond to security incidents.
- Threat Intelligence (TI)Collection and analysis of threat data.
- Vulnerability Management (VM)Detect and eliminate weak points in your own IT infrastructure.
- Penetration Testing and Red Teaming (PT)Simulate attacks on your own IT infrastructure to uncover weaknesses.
- Security Information and Event Management (SIEM)Consolidate and analyse security-relevant data from the entire organisation in a central location.
- User and Entity Behaviour Analytics (UEBA)Analyse the behaviour of users and entities to detect anomalies and weaknesses.
A Security Information and Event Management (SIEM)-system is therefore a Central component of a SOC. The SIEM system enables real-time monitoring of the entire IT infrastructure and helps to recognise and respond to threats at an early stage. Learn more here more about SIEM and how Swissmakers can support you in setting up and operating it.
The following (non-exhaustive) list describes which measures of the ICT minimum standard can (to a large extent) be fulfilled by a SOC with the above definition:
| Designation | Task | SOC |
|---|---|---|
| ID.RA-1 | Identify the (technical) vulnerabilities of your operating equipment and document them. | VM, PT |
| ID.RA-2 | Up-to-date information on cyber threats is obtained through regular dialogue in forums and committees. | TI |
| ID.RA-3 | Identify and document internal and external cyber threats. | VM, TI, SIEM, PT |
| ID.SC-4 | Establish a monitoring system to ensure that all your suppliers and service providers fulfil their obligations in accordance with the specifications. Have this confirmed regularly in audit reports or technical inspection results. | SIEM, UEBA |
| ID.SC-5 | Define response and recovery processes with your suppliers and service providers following cybersecurity incidents. Test these processes in exercises. | IR, PT |
| PR.IP-9 | Establish processes for responding to cyber incidents that have occurred (incident response planning, business continuity management, incident recovery, disaster recovery). | IR |
| PR.IP-10 | Test the response and recovery plans. | IR, PT |
| PR.IP-12 | Develop and implement a process for dealing with recognised vulnerabilities. | VM |
| PR.PT-1 | Define specifications for audits and log recordings. Create and check the regular logs in accordance with the specifications and guidelines. | SIEM |
| DE-AE-2 | Ensure that detected cybersecurity incidents are analysed in terms of their objectives and methods. | IR, SIEM |
| DE.AE-3 | Ensure that information on cybersecurity incidents from various sources and sensors is aggregated and processed. | SIEM, TI |
| DE.AE-5 | Define threshold values that are set for incident alerts. | SIEM |
| DE.CM-1 | Establish continuous network monitoring to detect potential cybersecurity incidents. | SIEM |
| DE.CM-2 | Establish continuous monitoring/surveillance of all physical assets and buildings to detect cybersecurity incidents. | SIEM, UEBA |
| DE.CM-3 | Employees' activities are monitored to identify potential cyber security incidents. | SIEM, UEBA |
| DE.CM-4 | Make sure that malware can be detected. | SIEM, TI |
| DE.CM-5 | Ensure that malware can be detected on mobile devices. | SIEM, TI |
| DE.CM-6 | Ensure that the activities of external service providers are monitored so that cybersecurity incidents can be detected. | SIEM, UEBA |
| DE.CM-7 | Continuously monitor your systems to ensure that activities/access by unauthorised persons, devices and software are detected. | SIEM |
| DE.CM-8 | Perform vulnerability scans. | VM |
| DE.DP-4 | Communicate detected incidents to the responsible parties (e.g. suppliers, customers, partners, authorities, etc.). | IR |
| RS.RP-1 | Ensure that the response plan is implemented correctly and promptly during or after a detected cybersecurity incident. | IR |
| RS.AN-1 | Ensure that notifications from detection systems are taken into account and investigations are triggered. | IR |
| RS.AN-3 | Carry out forensic analyses after an incident has occurred. | SIEM, IR |
| RS.AN-5 | Set up processes to receive, analyse and respond to vulnerabilities that the organisation becomes aware of from internal and external sources (e.g. internal audits, security bulletins or security researchers). | TI |
| RS.MI-1 | Ensure that cybersecurity incidents can be contained and further propagation interrupted. | IR |
| RS.MI-2 | Ensure that the impact of cybersecurity incidents can be mitigated. | IR |
| RS.MI-3 | Ensure that newly identified vulnerabilities are reduced or documented as accepted risks. | VM |
The list of measures is by no means complete, but it clearly shows how important the use of a SOC and therefore also a SIEM is for electricity suppliers. Practically all required measures from the ICT minimum standard can ensured or at least supported by a SOC become.
Sources and further information:
Free advice
Conclusion
The implementation of a Security Operations Centre (SOC) is essential for Swiss electricity suppliersto fulfil the mandatory requirements of the ICT minimum standard from July 2024. A SOC offers comprehensive security monitoring, rapid incident response and effective vulnerability management, supported by a centralised SIEM system.
Swissmakers has the following Many years of experience in the support of SIEM systems for energy suppliers and offers specialised solutions based on Elasticsearch, which form a robust basis for automatically analysing and monitoring security-relevant events. The SOC-lite service from Swissmakers takes over the maintenance and monitoring of the SIEM environment, analyses alarms and provides support in the event of security-related incidents. This allows energy suppliers to concentrate on their core business while the experts from Swissmakers protect their IT infrastructure.