Real-time monitoring SIEM
Your customised SIEM with Elasticsearch
With our SIEM system, you can significantly improve the security of your company:
Interesting for you:
Official partner:
Awareness
As a company, you have to be aware of the fact that Cyber threats in this day and age omnipresent are. Organisations of all sizes are increasingly being targeted by cyber criminals who want to steal or damage their data, systems and customer information. To protect your corporate IT from these threats, you need an effective solution that provides visibility - this is where SIEM systems come into play.
SIEM?
SIEM stands for Security Information and Event Management. The aim of a SIEM is to be able to react as quickly and precisely as possible to threats or specific log messages/events. This gives IT managers a powerful tool that enables them to react immediately and not just when it is basically already too late. To this end, SIEM systems attempt to make attacks or attack vectors visible in real time by collecting logs from a central location across the company, analysing them automatically and issuing alerts.
The following components are often integrated as information sources for a SIEM:
- Linux and Windows servers
- Active Directory, Domain Controller
- Firewalls, proxies
- Routers, switches
- Logstash
You can find an overview of all integrations here.
The Elastic Agents are also recommended. They are autonomous computer programmes that have been specially designed for the pre-sorting and transmission of specific log data. These include the following:
In the SIEM system (Elasticsearch), the information is then stored by the agents in a structured manner and also brought into relation to each other. Together with our approx. 900 predefined starter security rules, this forms the basis for constant and automatic analysis of your logs. Vendor-specific rules can also be modified, created or imported. All data from the complete SIEM can also be viewed and manually searched at any time by authorised persons via Kibana (webUI).

Date
Arrange a non-binding initial consultation
Blog posts about SIEM:
Our solutions
ELK setup
approx. 5 person days
Scoping & sizing of the environment
Concept & project planning
Configuration of the Linux server
Installation Elasticsearch cluster
Creation of lifecycle policies
Installation of Logstash and Kibana
SELinux-Security hardening of the platform
Documentation and acceptance (optional training)
Starter SIEM
approx. 8 - 10 person days
ELK setup
Setting up the recommended Top 1000 Detection Rules
Deployment of a Fleet Server
Extend Kibana redundantly as an HA construct
Integration of threat intelligence data
Monitoring the Active Directory server
Configuration of incident alerting to your security team
Standard SIEM
approx. 12 - 15 person days
Starter SIEM
Deployment of all detection rules
Configuration of Logstash with GeoIP
Create custom input rules
Integration of Filebeat & other beats
Perimeter firewall integration
Template creation for monitoring all Windows systems (server / clients) of your company
Our expertise - your SIEM
SOC-lite Service
SIEM needed, but no resources available? Our SOC-lite service relieves you by professionally maintaining and monitoring your SIEM environment. We ensure that alarms are analysed effectively and provide you with targeted support in the event of security-relevant incidents. Leave the technical expertise to us while you concentrate on your core business.
The Kibana user interface
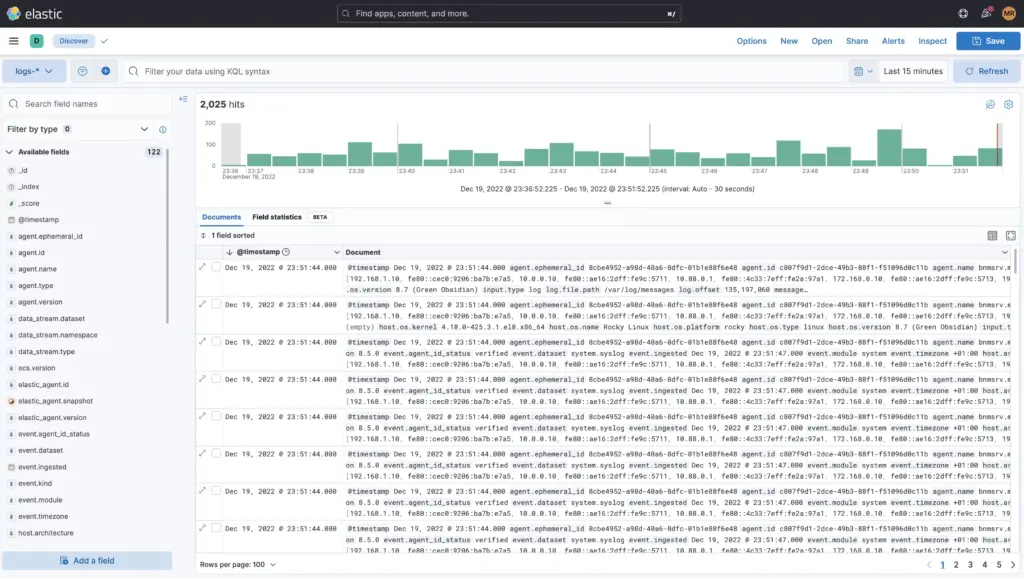
Search quickly and easily like on Google
Searching in Kibana (UI of Elasticsearch) is done by a simple full-text search, by clicking together the desired data fields in relation to something or a specific time or, most simply, by writing KQL (Kibana Query Language) search queries. These types of queries are very precise and easy to learn. This gives you a complete overview of your entire IT, your servers and clients, with maximum accuracy and flexibility.
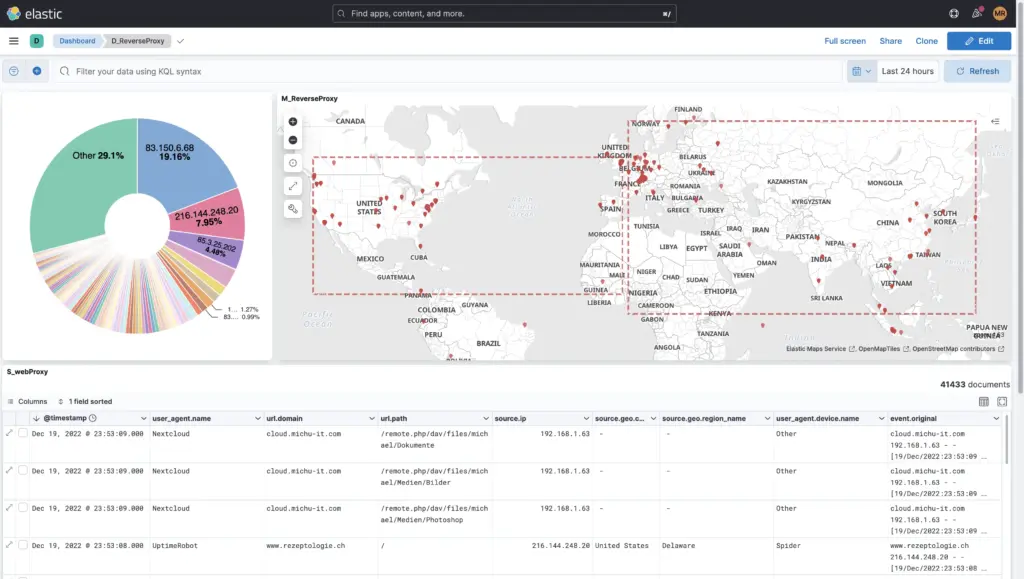
Meaningful charts and analyses
Kibana's informative charts and analysis elements offer a wide range of visualisation options when creating your own overview boards. Dashboards such as the one above for a reverse proxy make it possible to quickly and easily track, interpret and analyse connections, security breaches and access on a geo-based basis. This allows you to make quick and reliable reactive decisions.
Added value for your company?
A SIEM system offers you numerous advantages. Firstly, you can actively create a complete overview of all your company's technical assets in real time. Secondly, the system actively helps to minimise the risks of undetected cyberattacks and identify potential security vulnerabilities at an early stage before they can be exploited.
By continuously evaluating all logs, you can protect your data and systems against unauthorised data theft and detect malware or unauthorised processes as soon as they are started. SIEM systems also help to fulfil compliance requirements and automatically secure evidence and activity of all IT processes in the company.


SIEM made to measure
Our SIEM systems are designed to be easily customisable for companies of all sizes and industries. We offer you 10 years of expertise in customised solutions that are tailored to the specific needs and requirements of each individual customer.
In addition to SIEM engineering, we also offer training and support to ensure that you, our customers, can utilise the full potential of your SIEM system.
Conclusion
In short, if you want to protect your company's IT efficiently and securely and also create visibility across all systems, a SIEM system is an indispensable tool.
Our team of experienced security experts and engineers are ready to help you find and install the right SIEM system for your needs. Contact us today to learn more about our SIEM solutions and how we can help you protect your data and systems from cyber threats.